This is your sign to turn on 2FA now

00 INTRO
“Oh great, another reminder to set up 2FA. Do they really have to hassle me about it every time? I mean, come on, who’s got the patience for that?”
Tell me, how many times did you say (or think) some version of this sentence? I know I did! We all have. Reason? Well, no one likes the idea od having to do something twice to get what they want.
But think about it this way: if you lost your house or car keys, you wouldn’t just shrug it off, right? Because you know there’s a chance someone could use that key to get into your property. So you move quickly to change all the locks, right away.
Now, what if you could get a ping on your phone every time someone tried to use your house key? You’d have the power to say “Nope, not today!” and keep your posessions safe. Sure, you’d still change those locks eventually, but at least your belongings stay secure in the meantime.
See where I’m going with this? That’s the beauty of online 2-factor authentification – it’s like having an extra layer of security for your digital life.
01 The basics
How many steps?
“Okay, so is it 2-step verification, or should we call it 2SV? Or wait, maybe it’s 2FA? What do you mean MFA? Multi FA? There’s more than two?”
First, I hope I got you on board with stepping up your account security, because we’ve hit our first hurdle. The naming is all over the place.
But no matter what it’s called, the goal is the same – keeping your accounts safe from attacks.

Theory
Alright, let’s dive into the theory behind 2-step verification, or as we’ll refer to it from now on, 2FA. Basically, 2FA is a security setup where you have to prove you’re you in two different ways. These ways are what we call factors – that’s wha tthe ‘F’ stands for. And the ‘A’? Well, that’s for authentication.
2FA is one aspect of Multi-factor authentication, with only two factors. You’ll find some online services that offer even more steps. While more factors generally mean tighter security, finding the sweet spot is key. You’ll want to tailor your security settings to strike that balance between convenience and protection, especially for your most sensitive accounts.
The factors
With 2FA, your first step is usually entering your password. That’s pretty standard for most of the services we use every day. We call this the knowledge factor, it’s something you know.
Back in the early days of the internet, people thought passwords were enough. Then, no one expected that we would have dozens of accounts on different online services. Which resulted in:
- using the same password everywhere
- one gets leaked, everything gets leaked (don’t do this ❌)
- having multiple passwords, or one for each online service
- no one can remember all of these, so you either create small variations of the same one (easily guessed when you have one) or you start writing them on post-it’s (don’t do this either please ❌)
So, what do we do instead? Add the second factor!
Depending on the 2FA options offered by online services, you’ve got a few different choices for that second step:
- SMS or call verification, authentication apps – classified as possession factors due to usage of personal mobile devices
- fingerprint, face and voice recognition – classified as biometric factors
- geographical position restrictions (availability in specific countries and places) – location factors
- and other less common ones in online usage like time factors – ability to login in specific times
Not all of these are used for online authentication, but the first two are pretty common.

03 How it works
Where do I fit in?
With the ongoing surge in cyberattacks targeting personal accounts and data, big names like Google and Microsoft insist on 2FA before letting you use their services. But let’s not wait for the big shots to tell us what’s essential. Let me walk you through how easy it is to stay secure online.
When you hear “2FA,” you might think of those SMS codes. But guess what? They’re not as safe as they seem. SMS messages aren’t encrypted, they can be easily intercepted in the network. And scammers are getting clever with SIM swapping, convincing your phone service provider to switch your phone number to a new SIM card. So, let’s ditch the risky methods and talk about authenticator apps.
Authentificator apps
They give you a 6-8 digit code that you can enter as your second step for authentication. But how does that actually work?
First off, open up one of your go-to online services and see if they offer 2FA with an authenticator app. Then, follow these steps – pretty much the same for any authenticator app out there:
- initiate the 2FA setup with authentication app on your online service
- download an authentication app of sorts if you haven’t already – two of the most common ones are Microsoft Authenticator and Google Authenticator
- open the app and scan the QR code that your online service showed you
- and that’s it 😀
From now on, your second verification step will be to open the app and enter the code from the app to the service you’re logging in to.
Behind that magic is a simple algorithm called Time-based One-time Passwords, or TOTP. This is how it works.
When you scan the QR code, it sets up a secret algorithm between your app and the online service. This algorithm generates unique codes based on the current time of day. So when you need to enter a code, both your app and the service already know what to expect. This removes the necessity for the authenticator app to communicate with all the services it authorizes, hence the security. 💪
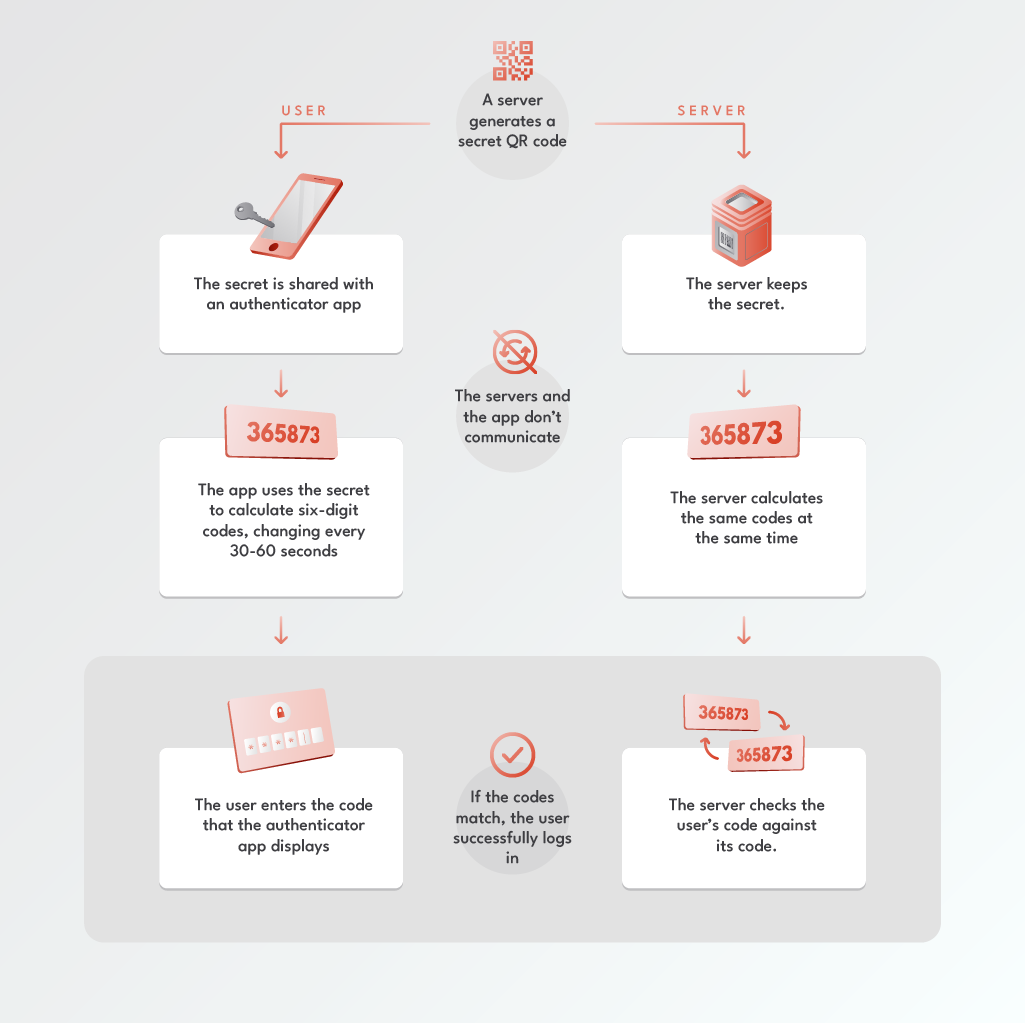
Image is based on the explanation from keepersecurity.com
Now you’re safe!
Additionally, it’s worth mentioning that authenticator apps often offer a secure option to back up your authenticated services to the cloud. This ensures that if you ever change or lose your phone, you won’t lose access to your accounts.
04 2fa 4life
Okay, how fast can I set it up?
As evident from the steps outlined above, setting this up couldn’t be simpler. Let’s say you can set it up for your LinkedIn account in just 2 minutes. The same amount of time goes for adding it to your email client, Google account, and social networks like Instagram or X. Even if you take your time with each, it shouldn’t take more than 15-20 minutes in total.
So, why not take care of it now while it’s fresh in your mind? With just two steps, you’ll be safer online and kiss those annoying pop-ups goodbye.
I’d say it’s definitely worth your time. 😀


